Skip to main contentThe Blacklist feature blocks agents from executing certain commands during task execution. This is useful for preventing problematic operations like calling unstable endpoints, using uninstalled tools, or running destructive commands.
When an agent tries to execute a blacklisted command, 2501 checks it against your defined patterns and rejects it if there’s a match, prompting the agent to find another approach.
Managing Blacklists
Go to Accounts → Blacklist and click Create Command to add a new entry.
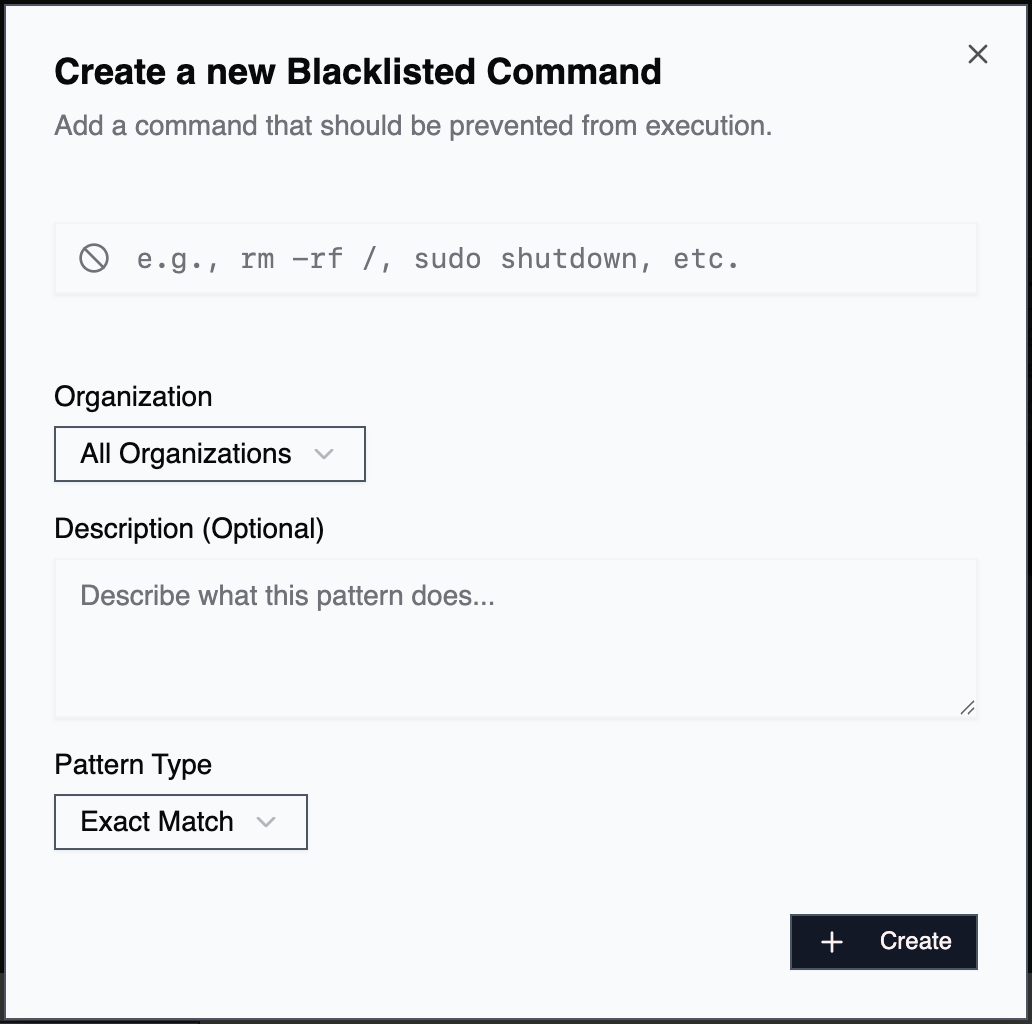
Pattern
A regex pattern that defines which commands to block.
Example: vim blocks the Vim text editor
Description
Explains why the command is blocked.
Example: Vim is interactive and can't be operated by LLMs
Organization
By default, blacklists apply to all organizations. Select a specific organization to restrict the blacklist to only that org’s agents.
Pattern Type
How the pattern matching works:
- Exact match: Command must exactly match the pattern
- Prefix match: Command must start with the pattern
- Contains: Pattern can appear anywhere in the command
Common Use Cases
Destructive Operations
Block high-risk commands for additional safety:
rm -rf /awscli terminate-instancessudo shutdown
Interactive Tools
Agents can’t interact with prompts or shells:
redis-cli (exact match) - Use redis-cli KEYS * style commands insteadvim, nano, vimysql, psqlpython (without arguments)
Missing or Unstable Tools
Block commands for tools that aren’t installed, have known issues, or are deprecated.
Best Practices
Use the most specific pattern type you can (exact match is better than contains). Document why each command is blocked. Review your blacklist regularly as your infrastructure changes.
For enforcing preferred alternatives instead of just blocking, see Operational Rules. 

